Introduction
Passwords kind of suck. We’ve known that for decades. Now, we finally have a credible replacement: passkeys. But how did we get here, and what’s next?
Personal Context
My own interest in authentication didn’t start in enterprise IT—it started back in the mid-2000s when I discovered KeePass. That little password vault kept my growing list of logins from turning into a Notepad security disaster.
Around 2009, I switched to LastPass, which had only just launched publicly the year before. Back then, it felt like magic—secure sync across devices, browser integration, and a smoother workflow than KeePass offered. Not long after, I started looking at YubiKeys. At the time, I was using them for everything from second-factor logins to unlocking encrypted TrueCrypt (very historical and unsecure now, since replaced by Veracrypt) volumes. They supported both One-Time Passwords (OTPs) with a short press on the USB key, and a long static 64-character code with a long press.

Fast-forward to today, and we’ve gone from USB sticks and browser extensions to biometric logins like Windows Hello that can authenticate you with a glance or a fingerprint. Passkeys take that one step further—secure credentials tied to your device, synced across your ecosystem, and no master password required.
These days, I rarely type passwords at all—between Apple’s iCloud Keychain and Bitwarden’s autofill, most of it’s handled for me. Worst case, I copy-paste manually. But even then, we’re just managing a flawed system more efficiently—not replacing it. Passkeys could finally change that.
How We Got Here
The road to passkeys has been long, winding, and paved with half-baked password replacements.
First, there were just passwords. Every service wanted one. So we reused them, forgot them, picked weak ones, or relied on “Forgot password” links as a routine login strategy.
Password managers like KeePass, LastPass, and Bitwarden helped, but didn’t solve the core problem. They just made password-based security tolerable.
Then came the FIDO Alliance. U2F brought hardware keys like YubiKeys into the mix—strong cryptography, but not very user-friendly. FIDO2 and WebAuthn improved that by adding support for built-in authenticators like biometrics and PINs.
Still, adoption lagged. Device-bound credentials weren’t easy to sync. Recovery was awkward. And most users had no idea what any of it meant.
Passkeys change that. Same underlying tech, but better UX. And thanks to Apple, Google, and Microsoft backing the same model, the pieces are finally coming together.
What Are Passkeys, Really?
A passkey is a cryptographic key pair. The public key is stored by the website or service. The private key stays on your device.
When you log in, the site challenges your device to prove you have the private key. Your device signs the challenge—typically after biometric or PIN confirmation—and that signature is verified using the public key.
- No passwords
- No shared secrets
- No phishing risk (did someone say “Challenge accepted”?)
Your keys are protected by your device, synced through the cloud (iCloud, Google, or Microsoft), and encrypted end-to-end. There’s no master password to remember. And there’s no database of credentials for attackers to steal.
It’s not just more secure—it’s simpler.
The Current State of Passkeys
Today, passkeys are available across all major ecosystems—but with some differences in polish.
Apple has the smoothest implementation. If you use iCloud Keychain, passkeys are synced across your iPhone, iPad, and Mac. Face ID or Touch ID unlocks logins without typing anything.
Google supports passkeys through Google Password Manager. They work on Android and Chrome, syncing via your Google account. You can also use your phone to log in on desktop via QR code.
Microsoft has added native passkey support in Windows 11 (since 23H2), and it’s getting better. Windows Hello and Edge both support passkeys, and Microsoft accounts now allow you to sign in with them. The syncing story is improving too, although it’s still catching up to Apple and Google in terms of polish and integration.
Password managers like 1Password and Bitwarden have started rolling out passkey support, letting you store and use them across ecosystems—helping passkeys break out of the walled gardens.
The main blocker now is adoption. Many services still rely on passwords. Others offer passkeys, but hide the option in advanced settings. It’s improving, but slowly.
FIDO vs. Passkeys: What’s Really Happening?
Let’s be honest—FIDO hasn’t exactly been a hit with regular users. Great tech, but the experience wasn’t built for convenience.
Passkeys change that. They take the FIDO2 model and build a user experience on top that actually works: no extra hardware, no multiple enrollments, no “what if I lose my key” panic.
It’s still FIDO under the hood, but passkeys shift the focus from security for admins to security for everyone. And that makes all the difference.
That’s also why it can feel like FIDO is being left behind. But really, it’s just faded into the background. If you’re using a passkey, you’re using FIDO—you just don’t need to know it anymore.
Security keys still have their place, especially in enterprise or high-assurance environments. But for most users, synced, device-based credentials are good enough—and much easier to use.
FIDO isn’t dead. It’s just not the headline anymore.
Demo time: Try It Now
If you want to see what a passkey login actually looks like, without configuring a service you already use, or sign up for something you don’t need, visit https://webauthn.io.

It’s a demo site built on the official WebAuthn spec. You can register a passkey using your device’s built-in auth (Face ID, Touch ID, Windows Hello, etc.), and then log in again without using a password.
It doesn’t save any real data and doesn’t require an account. It’s just a simple way to try out passkeys on whatever setup you’re using.
Try it on your phone, then your laptop. If syncing works 🤞, you’ll see the magic.

I also tested some real-world scenarios with Sony and Microsoft accounts. Sony offer a smooth registration experience using biometrics (Face ID), and follow-up logins are just as seamless.
Microsoft’s passkey login also works cleanly using Face ID too (but defaulted to Passwordless Authenticator which isn’t bad going into it).
Here are a few screenshots from both tests, showing what passkey login actually looks like:
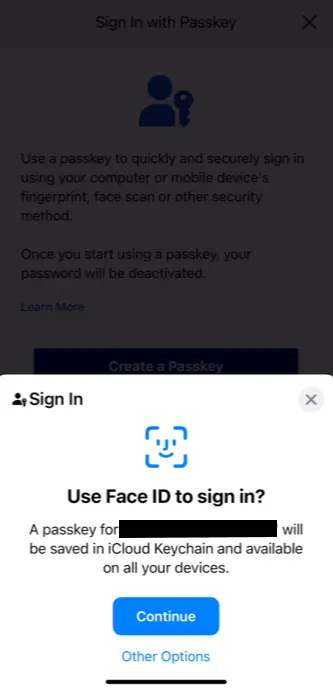
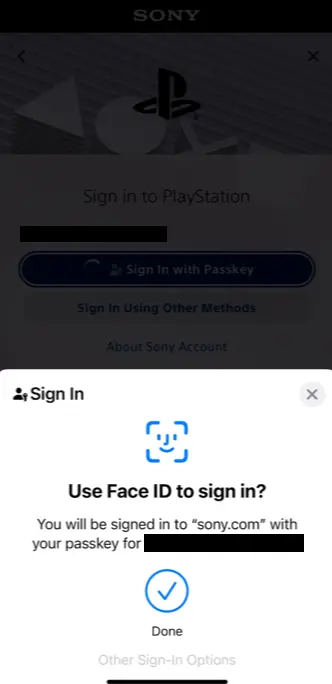
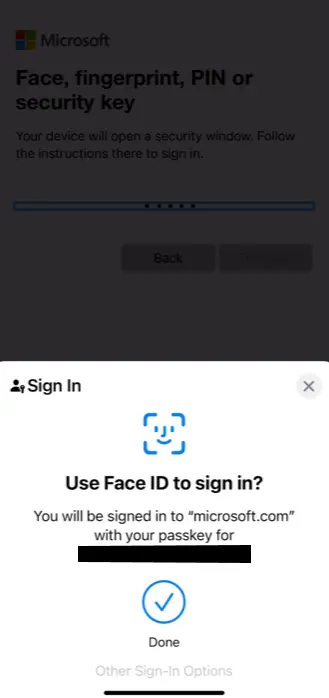
Conclusion: The Beginning of the End (for Passwords)
We’ve heard about the end of passwords before. This time, the replacement might actually stick.
Passkeys take strong, proven tech and wrap it in an experience that works. The result is something secure enough for enterprise, but simple enough for everyday users.
We’re not fully there yet. Many sites still allow fallback logins using a password and 2FA—even if you’ve registered a passkey. That undermines some of the security benefits. Until services start removing those old paths entirely, passkeys won’t be a silver bullet.
But we’re getting close. And for once, it feels like the password problem might actually have an expiration date.
What About You?
Have you tried using a passkey yet? Did it work the way you expected—or did something trip you up?
Let me know in the comments, or share what’s keeping you from making the switch.